The Open Shortest Path First (OSPF) protocol is a foundational component of modern networking. It’s […]
Networking Fundamentals: Border Gateway Protocol (BGP) explained
The Border Gateway Protocol (BGP) is one of the most critical components of the modern […]
Networking Fundamentals: A Deep Dive into the QUIC Protocol
The evolution of the internet has driven the need for faster, more reliable, and secure […]
Networking Fundamentals: SNMP (Simple Network Management Protocol) Explained
Simple Network Management Protocol (SNMP) is one of the foundational protocols in network management. It […]
Networking Fundamentals: Understanding ICMP
The Internet Control Message Protocol (ICMP) is a critical component of modern networking, designed to […]
Networking Fundamentals: A Deep Dive into ARP (Address Resolution Protocol)
Address Resolution Protocol (ARP) is a critical networking protocol that facilitates communication between devices within […]
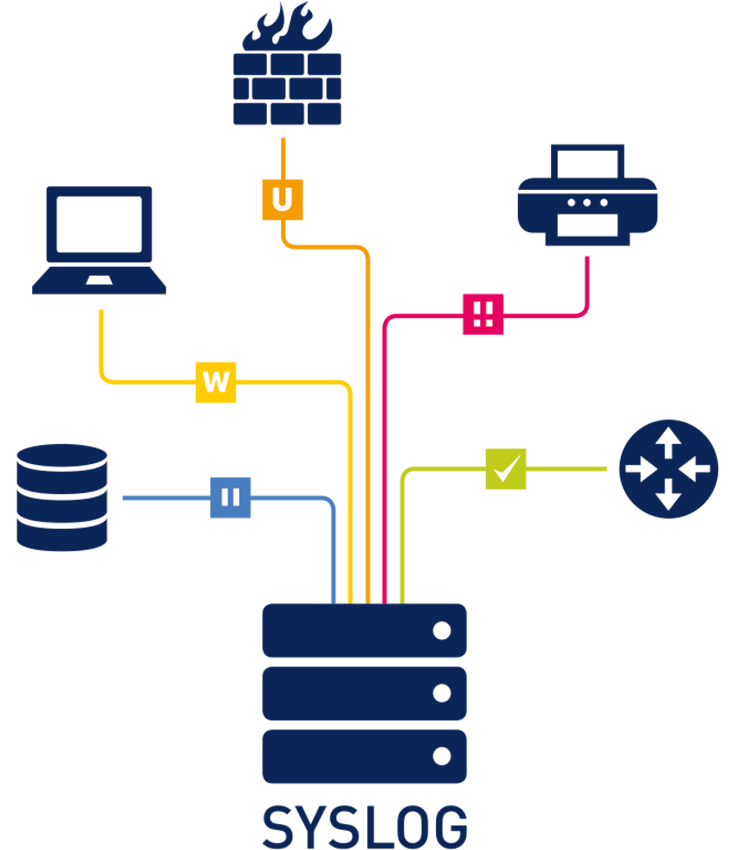
Syslog Simplified: Unveiling the Core of Logging and Monitoring
In today’s complex IT environments, managing and monitoring system events across a wide range of […]
MQTT Explained: How It Works, Practical Use Cases, and Security Best Practices
If you’ve ever been curious about how those smart home devices talk to each other […]
What is Packet Sniffing and how it works?
What is Packet Sniffing? Packet sniffing involves capturing, collecting, and logging network packets as they […]
What Is NetFlow? A Deep Dive into Its Functionality and Benefits
Understanding how data moves through your network is essential for ensuring optimal performance, robust security, […]