In today’s digital world, the need for secure communication has never been more critical. Whether you’re shopping online, sending an email, or streaming your favorite content, Transport Layer Security (TLS) plays a vital role in keeping your data safe from prying eyes. But what exactly is TLS, and how does it work to protect your information in transit? In this post, we’ll break down the complexities of TLS, making it easy to understand why it’s the backbone of secure online interactions. Let’s demystify TLS and explore how it safeguards our digital lives.
What is TLS?
TLS, or Transport Layer Security, is a cryptographic protocol designed to safeguard data transmitted over a network, such as internet traffic. It’s widely used to secure activities like email communication, VOIP calls, online transactions, file transfers, and instant messaging. TLS ensures that data remains private and intact, protecting sensitive information such as browsing activity, personal messages, passwords, account details, financial data, and even social security numbers from eavesdropping and tampering.
While TLS secures the transmission of data in transit, it doesn’t protect data at its endpoints or provide encryption for stored data.It is a security protocol specifically designed for HTTPS connections, not for insecure HTTP connections.
TLS History and Versions
Transport Layer Security (TLS) is the successor to the Secure Sockets Layer (SSL) protocol, originally developed by Netscape in 1994 to secure its browser, Netscape Navigator. The last SSL version, SSL 3.0, served as the foundation for the first version of TLS, which was introduced in 1999.
Although TLS replaced SSL, the terms SSL and TLS are often used interchangeably. This confusion stems from the fact that TLS 1.0 was initially referred to as SSL 3.1 during its development. As a result, many products and certificates marketed as “SSL” today actually use the TLS protocol. To address this overlap, the term “SSL/TLS” is commonly used to describe the protocol.
TLS Versions
- TLS 1.0: Released in 1999, based on SSL 3.0, it introduced improved security features.
- TLS 1.1: Released in 2006, it added enhancements like protection against certain cryptographic attacks.
- TLS 1.2: Introduced in 2008, it remains the most widely used version today, offering significant security improvements, including support for modern cryptographic algorithms.
- TLS 1.3: Published in 2018 by the Internet Engineering Task Force (IETF), TLS 1.3 simplifies the protocol, enhances performance, and eliminates outdated algorithms like SHA-1 and MD5.
Deprecation and Compatibility
SSL 3.0 was officially deprecated in 2015 due to vulnerabilities, but TLS provides limited backward compatibility for older devices that still use SSL. However, the landscape changed further in 2020 when major vendors like Apple, Microsoft, and Google ceased support for TLS 1.0 and 1.1. These versions relied on outdated cryptographic techniques, and their deprecation has led to error messages or blocks for websites that still use them.
Adoption Today
Most modern web applications rely on TLS 1.2 due to its robust security and widespread compatibility. While TLS 1.3 adoption is growing, it will take time to become the standard as organizations gradually update their systems. Legacy applications that don’t support newer TLS versions may use extensions like LS_FALLBACK_SCSV to maintain compatibility, although these workarounds are increasingly rare.
TLS Functionalities
TLS serves three primary purposes, with an additional practical benefit that enhances security:
- Encryption: TLS encrypts data exchanged between two parties—usually a client (like your browser) and a web server—ensuring that sensitive information remains private and protected from eavesdropping.
- Authentication: It verifies the identities of the communicating parties, preventing attackers from impersonating legitimate users or servers. This is key to safeguarding against impersonation attacks.
- Integrity: TLS ensures that the data transferred across the network hasn’t been altered during transit. By using certificates issued by trusted Certificate Authorities (CAs), it prevents tampering and protects against man-in-the-middle attacks.
- Replay Prevention: As an added layer of security, TLS defends against brute force and man-in-the-middle attacks by incorporating measures to detect and block replayed messages.
Where TLS is used?
TLS is widely used to secure application layer protocols such as FTP, HTTP, and SMTP, which underpin many of the internet’s essential functions like sending emails, chatting, and downloading data.
Beyond securing communication, TLS facilitates the authentication of digital identities. Common enterprise applications include single sign-on (SSO), verifying devices in IoT networks, digitally signing documents, encrypting emails to protect sensitive business information, and authenticating network access. These use cases highlight TLS’s critical role in ensuring secure and trusted interactions in both personal and enterprise environments.
Why TLS is used?
TLS encryption plays a crucial role in safeguarding internet applications against cyberattacks and data breaches. It has become the standard for secure connections in most popular web browsers. For instance, Google Chrome now warns users when accessing HTTP pages, flagging them as insecure. This shift has raised concerns among businesses, as such warnings can erode customer trust. To address this, tech giants like Google, Apple, and Microsoft strongly advocate for the use of at least TLS 1.2.
Earlier versions, TLS 1.0 and 1.1, are vulnerable to several high-profile attacks, including CRIME, BEAST, FREAK, LogJam, and POODLE. By contrast, TLS 1.2 and 1.3 offer robust protection during data transfers, incorporating advanced security measures that mitigate these vulnerabilities. For example, the Payment Card Industry Data Security Standard (PCI-DSS) mandates the use of TLS 1.2 or higher to meet compliance requirements.
TLS 1.2 and 1.3 also support modern cipher suites and cryptographic algorithms while eliminating outdated and insecure hash functions like SHA-1 and MD5. This ensures stronger, more reliable encryption, making these protocols essential for secure online interactions.
How does TLS handshake works?
A TLS handshake is the process that sets up a TLS session, but it is not the secure session itself. While the handshake does not encrypt data, it establishes the encryption method that will be used. Actual data encryption occurs during the session, utilizing a shared secret generated during the handshake.
The handshake starts by negotiating the TLS version and selecting an appropriate cipher suite—a combination of algorithms where each algorithm performs a specific function, such as encryption, authentication, or key exchange. The server determines the key exchange algorithm to be used at this stage.
To initiate the connection, the handshake relies on asymmetric encryption, which, while secure, is resource-intensive. This method uses a public key for encryption and a private key for decryption. In the context of TLS, the key pair is used to generate a shared key, also known as a shared secret, pre-master key, or master key. Once the handshake is successfully completed, this shared key becomes the session key, which is then used for encrypting subsequent communications.
During the session, symmetric encryption replaces asymmetric encryption. Symmetric encryption is significantly more efficient, as it imposes much lower computational overhead, ensuring a secure and fast exchange of data between the client and server.
Steps in an SSL/TLS Handshake (Pre-TLS 1.3)
Before the introduction of TLS 1.3, the handshake process involved the following steps:
- ClientHello: The client initiates the handshake by specifying supported TLS versions, cipher suites, and other settings.
- ServerHello: The server responds with its chosen TLS version and cipher suite.
- Certificate (optional): The server may provide its certificate to authenticate itself.
- ServerKeyExchange: The server sends additional key exchange information if required.
- ServerHelloDone: The server signals the end of its part of the handshake.
- ClientKeyExchange: The client sends its key exchange information.
- ChangeCipherSpec (twice): Both client and server signal that subsequent messages will be encrypted.
- Finished: Both parties confirm the handshake is complete and the secure session begins.

TLS 1.3 Simplifications
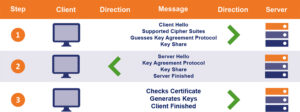
Similar to the TLS 1.2 handshake, the process in TLS 1.3 begins with a ClientHello message. However, this time, the message includes significantly more information. One notable change in TLS 1.3 is the reduction of supported cipher suites from 37 to just 5. We’ll dive into the details of this later, but in the context of the handshake, this means the client can make an educated guess about the key agreement/exchange protocol the server will use and include its key share for that guessed protocol.
The server responds with a ServerHello message (servers, as always, remain quite polite). At this stage, the server also provides its SSL certificate, much like in TLS 1.2. If the client’s guess was correct and both parties agree on the same AEAD (Authenticated Encryption with Associated Data) protocol, the server sends its portion of the key share, calculates the session key, and concludes with a ServerFinished message.
Armed with all the necessary information, the client then validates the SSL certificate and uses the key shares exchanged during the handshake to calculate its own copy of the session key. Once this is complete, the client finalizes the handshake by sending its ClientFinished message, marking the beginning of a secure, encrypted session.
TLS 1.3: Enhancements and Modernisation
TLS 1.3 was introduced to address several shortcomings of earlier versions, focusing on phasing out outdated and insecure technologies, improving security, enhancing performance, and simplifying the protocol. It eliminates unsafe algorithms, maintains backward compatibility for essential features, speeds up connections, and adopts a streamlined approach with fewer, more trusted cipher options.
Elimination of Legacy Algorithms and Ciphers
TLS 1.3 discontinues the use of several outdated cryptographic methods, such as the DES algorithm, RC4 cipher, SHA-1 hashing, CBC cipher mode, MD5 algorithm, RSA key exchange, and some Diffie-Hellman encryption methods. For comparison, TLS 1.2 supports 37 cipher suites, while TLS 1.3 narrows this to just 5, focusing on stronger, modern algorithms.
Move Away from RSA for Key Exchange
Traditionally, RSA was widely used for secure session key exchanges. However, RSA has fallen out of favor because it lacks support for ephemeral keys, which are essential for Perfect Forward Secrecy (PFS). PFS ensures that even if an attacker captures encrypted data and later obtains the private key, they cannot decrypt the information. By moving away from RSA key exchanges, TLS 1.3 prioritises forward secrecy and enhances long-term security.
Performance Improvements in TLS 1.3
TLS 1.3 introduces four key features to accelerate the handshake process:
- TLS Session Resumption: If the client and server have previously communicated, some security checks are skipped, reducing overhead.
- TLS False Start: Allows the client and server to begin transmitting data before the handshake is fully completed.
- Single Round-Trip Handshake: The handshake now requires only one round trip instead of the two needed in TLS 1.2. In earlier versions, the first round trip involved initial greetings, while the second was used for key exchanges and switching from asymmetric to symmetric encryption.
- Zero Round Trip Time Resumption (0-RTT): Enables the use of a pre-generated master resumption key, further minimizing latency for repeat connections.
Challenges and Considerations with TLS
For website owners, TLS can sometimes seem to impact website performance negatively. High traffic volumes or limited computing resources might make TLS appear to contribute to slower loading times. Additionally, misconfigured servers may inadvertently select weaker encryption methods, posing a potential vulnerability. Early implementations of TLS might also cause a temporary dip in website traffic as search engines reindex the site, and outdated add-ons or plugins might not be compatible with HTTPS, requiring further adjustments.
For general internet users, misunderstandings about how certificates work can contribute to perceived TLS failures. For instance, attackers can exploit expired or untrusted certificates. While browsers display warnings for such certificates, users often ignore these alerts, leaving them vulnerable to potential threats.
TLS’s design for robust end-to-end encryption can sometimes clash with certain security practices. For example, TLS may mistake firewalls or middleboxes for man-in-the-middle attacks, as it prevents any intermediary from inspecting encrypted traffic. While this is crucial for ensuring security, it also prevents network tools from detecting malware within the traffic. The financial industry, in particular, has pushed for changes to middlebox functionality to mitigate these challenges without compromising security.
Another vulnerability of TLS lies in downgrade attacks. Older versions of TLS and the now-deprecated RSA key exchange algorithm are susceptible to side-channel attacks. These indirect attacks exploit flaws in the cryptographic implementation, leaking enough information for an attacker to deduce the private key. This can be likened to a thief bypassing a car’s alarm system by towing the car away and breaking into it elsewhere. TLS 1.3 has eliminated RSA key exchanges to address these vulnerabilities, making the protocol significantly more secure.
Despite these challenges, TLS remains a cornerstone of secure online communication. Continuous updates to the protocol ensure that its security and performance keep pace with evolving threats, making it indispensable for protecting sensitive data and maintaining trust in the digital ecosystem.
Wrapping Up
The SSL/TLS handshake is a crucial process that quietly powers a secure internet. It works seamlessly in the background, ensuring safe connections without most people ever noticing it—until something goes wrong.
Feel free to share your thoughts or questions in the comments below!

Hello there, You’ve done an incredible job. I’ll certainly digg
it and personally recommend to my friends. I am confident they will be
benefited from this website.
This blog was… how do I say it? Relevant!! Finally I’ve
found something which helped me. Appreciate it!