Address Space Layout Randomization, or ASLR for short, is one of the most important computer […]
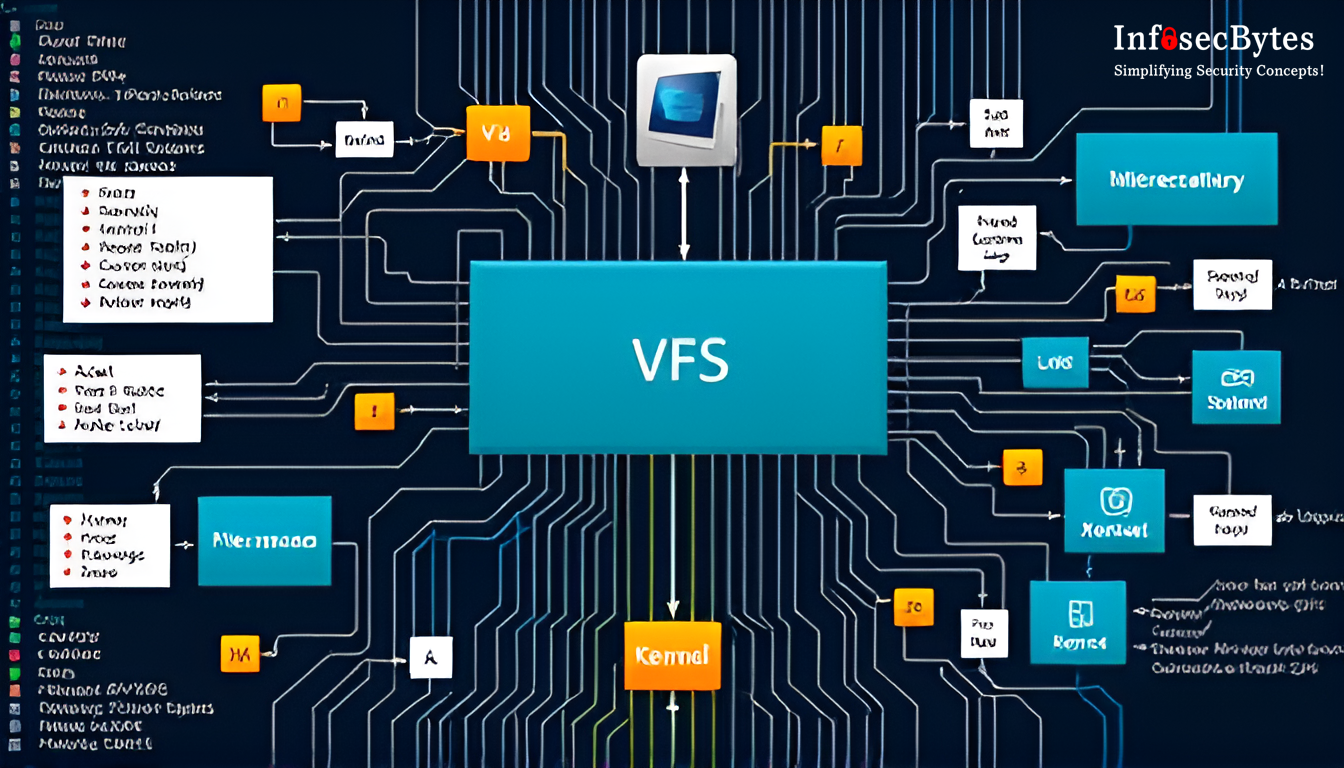
Linux Internals: Virtual File System
Imagine walking into a grand library where countless books are organized across different sections, languages, […]
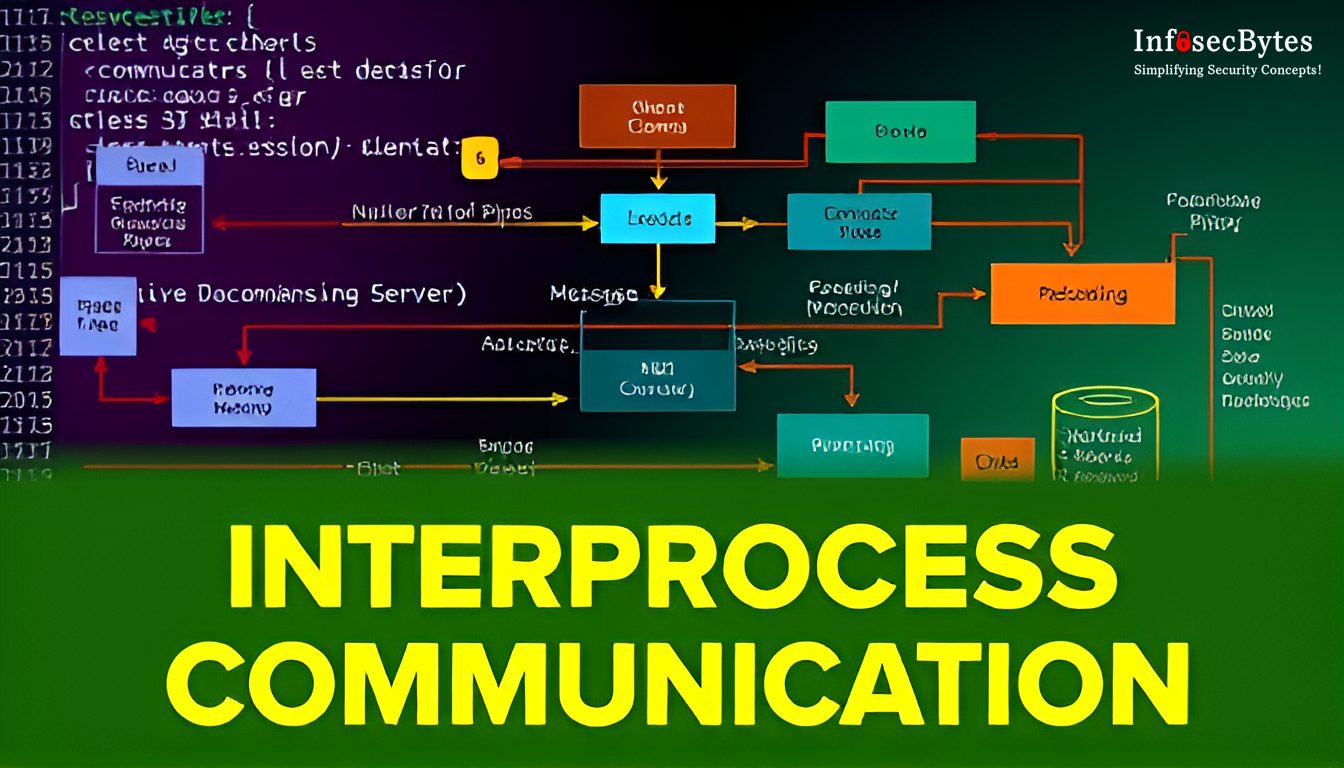
Linux Internals: Interprocess Communication
In the realm of operating systems, interprocess communication (IPC) is vital for allowing processes to […]
Linux Internals: Memory Management Explained
Memory management is a crucial aspect of any operating system, responsible for efficiently handling memory […]
Linux Internals: Process Management
Process management is one of the most fundamental aspects of an operating system. In Linux, […]
A Deep Dive into Protection Rings
Protection rings are a foundational concept in operating system (OS) design, essential for enforcing security, […]
Understanding SSH: History, Implementation, and Security Considerations
Secure Shell (SSH) is one of the most fundamental tools in the realm of network […]
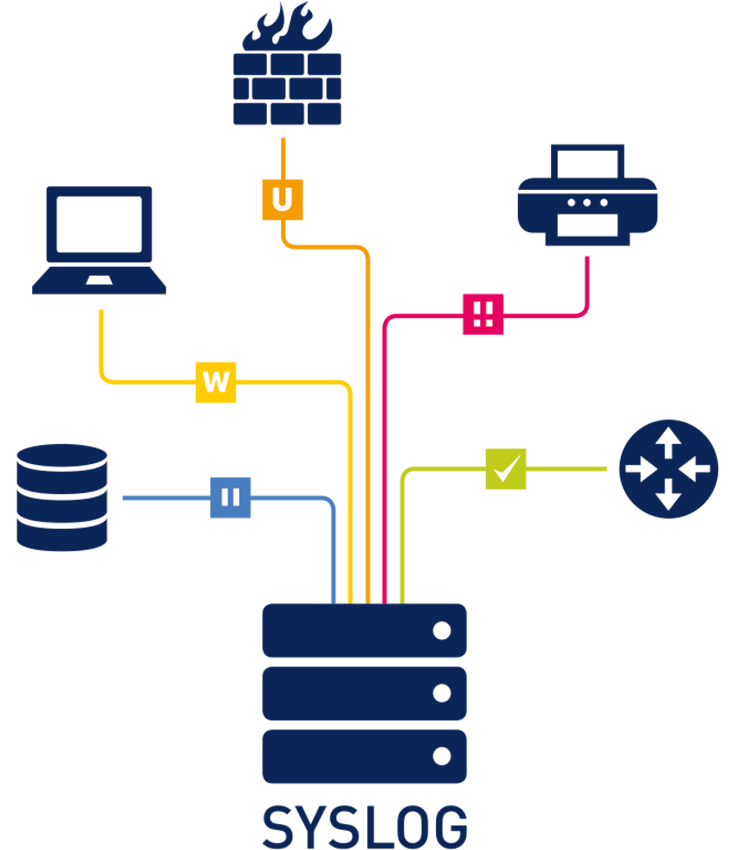
Syslog Simplified: Unveiling the Core of Logging and Monitoring
In today’s complex IT environments, managing and monitoring system events across a wide range of […]