In today’s cybersecurity landscape, securing communications over the internet is more crucial than ever. Transport Layer Security (TLS) has long been the standard for encrypting data in transit, protecting sensitive information from eavesdropping and tampering. However, traditional TLS only authenticates one party—the server—leaving potential security gaps. Mutual TLS (mTLS) addresses this limitation by ensuring that both the client and the server authenticate each other before establishing a secure connection.
This blog post explores what mTLS is, how it works, its security benefits, real-world use cases, and challenges in implementation.
What is mTLS?
Mutual TLS (mTLS) is an enhanced version of TLS that requires both the client and the server to present digital certificates for authentication. Unlike standard TLS, where only the server’s identity is verified, mTLS ensures a bidirectional trust mechanism, making it a crucial security measure for highly sensitive applications.
Why is mTLS Important?
- Prevents unauthorized access by authenticating both parties.
- Ensures encrypted and tamper-proof communication.
- Mitigates risks of man-in-the-middle (MITM) attacks and spoofing.
- Provides an additional layer of security beyond passwords or API keys.
How mTLS Works
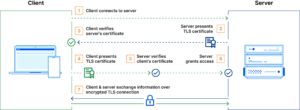
The mutual TLS handshake follows a similar flow to traditional TLS but includes an extra client authentication step. Here’s how it works:
1. Client Hello
The client initiates the connection by sending a ClientHello message to the server. This message includes:
- Supported TLS versions
- Cipher suites (encryption algorithms)
- A randomly generated number
2. Server Hello & Certificate
The server responds with:
- A ServerHello message, selecting the TLS version and cipher suite
- The server’s certificate (issued by a trusted Certificate Authority)
3. Client Certificate Request
Unlike traditional TLS, the server requests a client certificate to verify the client’s identity.
4. Client Certificate & Key Exchange
- The client sends its own certificate to the server.
- The client and server exchange session keys to encrypt further communication.
5. Server Verification & Secure Connection
The server verifies the client’s certificate. If successful, both parties establish a secure, encrypted communication channel.
Security Benefits of mTLS
Mutual TLS (mTLS) offers robust security advantages by enforcing bidirectional authentication, ensuring encrypted communication, and mitigating various cyber threats. Below are the key security benefits of implementing mTLS:
1. Stronger Authentication & Identity Verification
- Unlike traditional TLS, which only verifies the server, mTLS requires both parties (client and server) to present valid certificates, ensuring mutual trust before communication begins.
- Eliminates reliance on static credentials like API keys, passwords, or tokens, reducing the risk of credential theft, phishing attacks, and unauthorized access.
- Helps prevent session hijacking, credential stuffing, and brute-force attacks, as authentication is certificate-based rather than relying on user-input credentials.
2. Protection Against Man-in-the-Middle (MITM) Attacks
- Since both the client and server must authenticate each other using cryptographic certificates, attackers cannot impersonate either side, effectively blocking MITM attacks.
- Ensures that even if network traffic is intercepted, it remains encrypted and unreadable, safeguarding sensitive data during transmission.
- Provides an additional layer of security in zero-trust network architectures, where verifying every entity is crucial.
3. Improved Access Control & Least Privilege Enforcement
- Organizations can enforce stricter access policies by issuing client certificates only to authorized users, devices, or applications.
- Enables fine-grained access control, restricting access based on specific policies such as user roles, device type, or geographic location.
- Reduces the risk of insider threats by ensuring that only pre-approved clients with valid certificates can access sensitive resources.
4. Enhanced API Security & Secure Microservices Communication
- Many modern API-driven architectures, including microservices, Kubernetes clusters, and service meshes (e.g., Istio, Linkerd, Consul), leverage mTLS to encrypt service-to-service communication.
- Prevents unauthorized API requests, ensuring that only authenticated and trusted services interact within a distributed system.
- Eliminates the need for API keys or shared secrets, reducing the risk of API key leakage and making authentication more secure and scalable.
5. Stronger Data Privacy & Confidentiality
- mTLS ensures that all communication is fully encrypted, protecting sensitive data from eavesdropping and tampering.
- Ensures data integrity, preventing modification or injection of malicious payloads into network traffic.
Real-World Applications of mTLS
1. Zero Trust Security Architectures
- Google’s BeyondCorp model and other Zero Trust frameworks leverage mTLS for continuous authentication.
- Ensures only verified devices and users can access enterprise resources.
2. Secure API Communication
- Cloud service providers and fintech companies use mTLS to secure API-to-API communication, ensuring that only trusted clients can access critical services.
- Example: Stripe and PayPal require mTLS for payment API authentication.
3. Microservices Security
- In Kubernetes environments, mTLS secures service-to-service communication within clusters.
- Example: Istio service mesh uses mTLS to encrypt traffic between microservices.
4. Secure IoT Communications
- IoT devices use mTLS to verify both the device and the server, preventing unauthorized access to networks.
- Example: Medical devices transmitting patient data over the internet require mTLS for HIPAA compliance.
Challenges & Considerations When Implementing mTLS
While mTLS provides robust security benefits, it comes with operational challenges:
1. Certificate Management Complexity
- Requires a Public Key Infrastructure (PKI) to issue, revoke, and renew certificates.
- Organizations need tools like HashiCorp Vault, Let’s Encrypt, or AWS Certificate Manager.
2. Increased Overhead
- Every client needs a valid certificate, which adds management overhead.
- Performance impact due to additional authentication steps in the TLS handshake.
3. Scalability Concerns
- Managing thousands (or millions) of certificates in large-scale API or microservices environments can be challenging.
- Requires automation tools like Cert-Manager for Kubernetes.
4. Client Compatibility Issues
- Not all legacy systems support mTLS natively, requiring updates or workarounds.
Wrapping Up
Mutual TLS (mTLS) is a powerful security mechanism that enhances authentication, prevents unauthorized access, and ensures secure communication between clients and servers. With increasing security threats, organizations across finance, healthcare, cloud computing, and IoT are adopting mTLS to protect sensitive data and enforce Zero Trust principles.
However, implementing mTLS requires proper certificate management, automation tools, and compatibility checks to ensure smooth deployment. Despite its challenges, mTLS remains one of the most effective security measures for safeguarding modern digital infrastructures.

