The Linux kernel is the heart of the Linux operating system, serving as the critical interface between hardware and software. It manages system resources, enforces security, and ensures smooth operation by coordinating all hardware and software interactions. Understanding its architecture is key to grasping how Linux achieves its versatility, stability, and performance.
This article explores the Linux kernel architecture, its components, and how it functions to support a wide range of devices and workloads.
What Is the Linux Kernel?
The Linux kernel is a monolithic, open-source kernel initially developed by Linus Torvalds in 1991. It forms the core of the Linux operating system, managing hardware resources and providing essential services to user applications.
Unlike microkernels, which break functionality into smaller modules, the Linux kernel includes most core services (e.g., file system management, memory management) directly within the kernel space. Despite being monolithic, the Linux kernel supports modularity, allowing for dynamic loading and unloading of features at runtime.
Core Components of the Linux Kernel Architecture
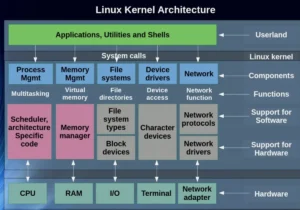
The Linux kernel is composed of several layers and subsystems, each responsible for specific tasks:
1. System Call Interface (SCI)
The SCI serves as the gateway between user-space applications and kernel services. Applications in user mode (Ring 3) cannot directly access hardware resources or execute privileged operations. Instead, they make system calls, which the SCI translates into kernel-level operations.
Common system calls include:
read()andwrite()for file operations.fork()for process creation.ioctl()for device-specific operations.
2. Process Management
This subsystem manages the creation, scheduling, and termination of processes. It ensures efficient CPU usage and prioritizes tasks using scheduling policies like:
- Completely Fair Scheduler (CFS): Provides fair CPU allocation among tasks.
- Real-Time Scheduling: Ensures time-critical tasks meet deadlines.
Key components include:
- Process Control Block (PCB): Stores information about processes, such as IDs, state, and resources.
- Task Scheduler: Allocates CPU time to processes based on their priority and scheduling policy.
3. Memory Management
Memory management ensures efficient allocation and deallocation of memory, preventing conflicts and ensuring system stability. It employs:
- Virtual Memory: Creates an abstraction layer between physical memory and processes, allowing each process to have its own address space.
- Paging: Divides memory into fixed-size pages for easier management and isolation.
- Swapping: Moves inactive memory pages to disk to free up physical memory.
Key data structures include:
- Page Tables: Map virtual addresses to physical memory.
- Kernel Slab Allocator: Optimises memory usage for frequently allocated objects.
4. File System Management
The Linux kernel supports various file systems, such as ext4, XFS, and NTFS. This subsystem manages file operations, ensuring data consistency and security.
Features include:
- Virtual File System (VFS): Abstracts file system implementation, providing a unified interface for user applications.
- Buffer Cache: Temporarily stores file system data to reduce disk I/O.
- Inodes: Represent metadata about files and directories.
5. Device Drivers
Device drivers are kernel modules that facilitate communication between the operating system and hardware. They abstract hardware details, exposing a standardised interface to user applications.
Types of device drivers:
- Character Drivers: Handle data streams (e.g., serial ports).
- Block Drivers: Manage block devices like disks.
- Network Drivers: Enable communication over networks.
7. Interrupt Handling
The kernel handles hardware interrupts (signals from devices) and software exceptions efficiently, ensuring quick responses to critical events.
Key components:
- Interrupt Request (IRQ) Lines: Connect hardware devices to the CPU.
- Interrupt Handlers: Special functions in the kernel that respond to specific interrupts.
- Bottom Halves: Defer non-critical work to be processed later, minimising delay in interrupt handling.
Kernel Modes and Privilege Levels
The Linux kernel operates using two distinct privilege levels to ensure security and stability:
1. Kernel Mode (Ring 0):
- The kernel runs in this highly privileged mode, granting it unrestricted access to hardware and critical system resources.
- All core system operations, such as memory management, process scheduling, and hardware control, occur in this mode.
2. User Mode (Ring 3):
- User applications and processes operate in this restricted mode with limited access to system resources.
- Any request for hardware interaction or privileged operations must go through the kernel via system calls.
This separation of modes acts as a safeguard, preventing errors or vulnerabilities in user applications from directly compromising the kernel or the overall system integrity.
Modularity in the Linux Kernel
While the Linux kernel is monolithic, it incorporates modularity to enhance flexibility and efficiency. Loadable Kernel Modules (LKMs) allow dynamic loading and unloading of kernel features, such as device drivers and filesystem support. This modular approach helps reduce memory usage and simplifies updates, as modules can be added or removed without requiring a reboot.
The management of kernel modules is facilitated through commands like:
insmod: Loads a module into the kernel.rmmod: Removes a module from the kernel.lsmod: Lists the currently loaded modules.
This modular design provides a balance between the performance benefits of a monolithic kernel and the flexibility of adding or removing functionality as needed.
Security Features of the Linux Kernel
The Linux kernel incorporates several advanced security features to safeguard the system against vulnerabilities and attacks:
1. Access Control
SELinux and AppArmor provide robust Mandatory Access Control (MAC) policies that restrict what processes can access, preventing unauthorised access to system resources.
2. Memory Protection
Techniques like Address Space Layout Randomization (ASLR) and stack canaries enhance memory security by making it more difficult for attackers to predict memory locations, thus preventing buffer overflow exploits.
3. Containerization
Cgroups and namespaces enable process and resource isolation within containers, ensuring that applications run in isolated environments with limited access to the rest of the system. This minimises the potential damage from security breaches.
4. Kernel Hardening
Tools like Grsecurity and the Kernel Self-Protection Project (KSPP) implement additional security measures, including patching kernel vulnerabilities, preventing privilege escalation, and strengthening overall kernel integrity.
Advantages of the Linux Kernel Architecture
The Linux kernel architecture offers several key advantages that make it a popular choice for diverse computing environments:
1. Performance
The monolithic design of the kernel reduces communication overhead between its components, ensuring efficient resource management and faster execution.
Flexibility
The modular nature of the kernel allows easy customization and the addition of new features, enabling administrators to tailor the system to meet specific needs without affecting core operations.
Compatibility
The Linux kernel supports a wide range of hardware and file systems, ensuring seamless integration with various devices and platforms.
Security
With its robust privilege separation, along with advanced security mechanisms like SELinux, AppArmor, and ASLR, the kernel is designed to protect the system from threats and vulnerabilities effectively.
These advantages make the Linux kernel highly adaptable, secure, and efficient, ensuring its continued success across different use cases, from embedded systems to enterprise servers.
Challenges and Limitations
Despite its many advantages, the Linux kernel architecture has its own set of challenges:
1. Complexity
The large and intricate codebase can make maintenance and debugging difficult, requiring careful management and constant updates to ensure system stability.
2. Resource Usage
As a monolithic kernel, it can consume more memory and resources compared to microkernels, which can impact performance in resource-constrained environments.
3. Vulnerability Exposure
Given the kernel’s central role in managing system operations, any exploit targeting the kernel can have severe consequences, potentially compromising the entire system.
Wrapping Up
The Linux kernel’s architecture is a testament to engineering excellence, combining efficiency, security, and flexibility to power a wide array of devices—from embedded systems to high-performance supercomputers. Its well-structured, modular design and robust subsystems ensure consistent performance while adapting to the ever-changing landscape of technology. Understanding the intricacies of the Linux kernel is essential for anyone seeking to explore Linux internals, optimize system performance, or build more secure and efficient computing environments.

