System calls, commonly referred to as syscalls, are the backbone of communication between user space and kernel space in Linux. They are the fundamental interface through which user applications request services from the operating system kernel. Without syscalls, user programs would be unable to perform critical operations such as reading files, allocating memory, or interacting with hardware.
In this article, we’ll explore syscalls in depth, including their definition, implementation in Linux, common types, , security considerations, and challenges.
What Are Syscalls?
System calls, or syscalls, are predefined functions that serve as a critical interface between user-level applications and the operating system kernel. They allow user applications, which run in user mode (Ring 3) with restricted privileges, to request services or access system resources controlled by the kernel, which operates in kernel mode (Ring 0) with unrestricted access to hardware and critical resources.
Syscalls act as gatekeepers, ensuring secure and controlled transitions between user mode and kernel mode for privileged operations. For instance, when a program needs to read data from a file, it cannot interact with the hardware directly. Instead, it invokes a syscall such as read(), which passes the request to the kernel. The kernel performs the operation and returns the result to the application, maintaining both system security and operational efficiency.
Why Are Syscalls Necessary?
Syscalls are indispensable in modern operating systems, providing the essential bridge between user applications and the kernel. Their necessity stems from several key functions:
1. Controlled Access to Resources
Syscalls serve as a gatekeeper, ensuring that user applications can access system resources—such as hardware, memory, and I/O devices—only in a controlled and secure manner. This prevents unauthorised or unsafe interactions.
2. Simplified Abstraction
By abstracting the complexity of low-level hardware operations, syscalls provide developers with an intuitive and consistent interface to interact with system resources, regardless of the underlying hardware architecture.
3. Ensuring Stability and Security
Syscalls maintain a clear separation between user applications and the kernel. This isolation minimises the risk of accidental or malicious interference with critical system components, ensuring system stability and security.
Implementation of Syscalls in Linux
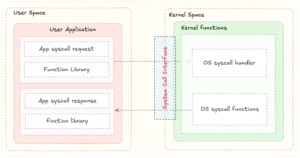
The implementation of syscalls in Linux is a well-optimised process designed to enable secure and efficient communication between user space and kernel space. Below are the key aspects of syscall implementation in Linux:
1. User Space Interaction
- Standard Libraries:
- Developers rarely interact with syscalls directly. Instead, they use standard libraries like glibc that abstract the complexities of invoking syscalls.
- For example, when a developer calls
printf(), it internally invokes thewrite()syscall to output data.
2. Transition via Trap Mechanisms
- Syscall Instruction:
- Modern x86-64 architectures use the
syscallinstruction to switch from user mode (Ring 3) to kernel mode (Ring 0). - Older x86 systems relied on software interrupts, such as
int 0x80, to achieve this transition.
- Modern x86-64 architectures use the
- Register Usage:
- The syscall number and arguments are passed via specific CPU registers:
rax: Holds the syscall number.rdi,rsi,rdx,r10,r8,r9: Hold the arguments for the syscall.
- The syscall number and arguments are passed via specific CPU registers:
3. Kernel Execution
- Syscall Table:
- The Linux kernel maintains a syscall table, which maps syscall numbers to their corresponding handler functions.
- This table is architecture-specific. For example, on x86-64 systems, it can be found in the file:
arch/x86/entry/syscalls/syscall_64.tbl
- Handler Function Execution:
- Once the syscall number is identified, the kernel executes the associated handler function to perform the requested operation, such as reading from a file or creating a process.
4. Returning to User Space
- Result Handling:
- After completing the operation, the kernel places the result or an error code in a designated CPU register (e.g.,
rax) before returning control to the user application.
- After completing the operation, the kernel places the result or an error code in a designated CPU register (e.g.,
- Mode Transition:
- The CPU switches back from kernel mode to user mode, ensuring that the application resumes execution in a safe and controlled manner.
5. Architecture-Specific Optimisations
- Fast Path Execution:
- Modern Linux kernels implement optimised paths for frequently used syscalls to minimise overhead and improve performance.
- Compatibility Layers:
- The kernel includes compatibility layers for legacy architectures and applications, ensuring backward compatibility with older syscall implementations.
By leveraging this efficient and secure design, Linux syscalls provide the foundation for robust communication between user applications and the kernel, ensuring stability and performance across diverse use cases.
Common Syscalls in Linux
Linux provides a rich set of system calls that allow user applications to interact with system resources and perform various operations. Here are some of the most commonly used syscalls, categorised by their functionality:
1. File Operations
Syscalls that deal with file creation, reading, writing, and deletion.
open(): Opens a file or device.read(): Reads data from an open file or device.write(): Writes data to an open file or device.close(): Closes an open file or device.unlink(): Deletes a file or symbolic link.
2. Process Management
Syscalls for creating, managing, and terminating processes.
fork(): Creates a new process by duplicating the calling process.execve(): Replaces the current process image with a new program.wait(): Waits for a child process to terminate.kill(): Sends a signal to a process to terminate or perform a specific action.
3. Memory Management
Syscalls to allocate and manage memory.
mmap(): Maps files or devices into memory.brk(): Adjusts the size of the process’s data segment.munmap(): Unmaps a previously mapped memory region.
4. Network Operations
Syscalls for socket creation and network communication.
socket(): Creates a socket for communication.bind(): Assigns a socket to a local address.connect(): Establishes a connection to a remote address.send(): Sends data through a socket.recv(): Receives data from a socket.
5. System Information
Syscalls to retrieve information about the system or current process.
uname(): Provides information about the operating system.getpid(): Returns the process ID of the calling process.gettimeofday(): Fetches the current time of day.
6. Inter-Process Communication (IPC)
Syscalls for communication between processes.
shmget(): Allocates shared memory.shmat(): Attaches a shared memory segment to the process’s address space.semop(): Performs operations on semaphores.msgsnd(): Sends a message to a message queue.
Security Considerations
Syscalls serve as a vital security boundary between user space and kernel space, playing a crucial role in maintaining the integrity and stability of the Linux operating system. However, improper handling or exploitation of syscalls can result in severe vulnerabilities, including privilege escalation, information leakage, or denial-of-service (DoS) attacks. Below are key security mechanisms and practices to mitigate risks associated with syscalls:
1. Input Validation
The kernel rigorously validates all arguments passed to syscalls to prevent:
- Buffer Overflows: Protects against memory corruption by ensuring input sizes stay within safe bounds.
- Invalid Memory Access: Ensures user processes do not access restricted or invalid memory regions.
2. Mitigating Syscall Abuse
- Secure Computing Mode (seccomp):
- A powerful Linux kernel feature that restricts the set of syscalls an application can invoke.
- By enabling seccomp, administrators can drastically reduce the attack surface, ensuring applications operate within a predefined syscall whitelist.
3. Sandboxing
- Containerization Tools:
- Technologies like Docker and Flatpak leverage syscall restrictions to isolate applications from the host system.
- Sandboxing ensures that even if an application is compromised, it cannot affect the broader system.
4. Patching and Updates
- Kernel Vulnerabilities:
- Syscall implementations are frequently targeted by attackers. Regular kernel updates address these vulnerabilities by patching known issues.
- Keeping the kernel and associated libraries up to date ensures that the system remains protected against emerging threats.
Challenges with Syscalls
1. Performance Overhead:
Transitioning between user mode and kernel mode introduces latency, which can impact performance in syscall-intensive applications.
2. Compatibility Issues:
Changes to syscall interfaces can break compatibility with older applications, requiring careful versioning and maintenance.
3. Complexity in Debugging:
Tracing syscall-related issues can be challenging, especially in large and complex systems. Tools like strace are invaluable for troubleshooting.
Tools for Analysing Syscalls
strace:
Monitors and logs syscalls made by a process, providing insights into its behaviour.
ltrace:
Similar to strace, but focuses on library calls made by an application, including syscalls invoked via standard libraries.
Perf Tools:
Performance monitoring tools like perf can analyse syscall latency and frequency, helping optimise applications.
Seccomp Tools:
Frameworks like seccomp-bpf allow fine-grained control over allowed syscalls for sandboxing applications.
Modern Enhancements and Alternatives
1. eBPF (Extended Berkeley Packet Filter):
eBPF allows user-space programs to safely execute in kernel space without requiring traditional syscalls. It provides high-performance packet filtering, tracing, and monitoring capabilities.
2. Direct System Call Bypass:
Some high-performance systems bypass traditional syscalls using shared memory or kernel bypass techniques to reduce overhead.
3. System Call Aggregation:
Techniques like batching multiple syscalls into a single operation improve performance by reducing context switches.
Syscalls form the foundation of interaction between user applications and the Linux kernel, providing a secure and efficient mechanism for accessing hardware and system resources. Their design ensures isolation between user applications and critical kernel operations while offering developers a versatile interface. However, syscalls come with challenges such as performance overhead and security vulnerabilities, highlighting the importance of careful management, monitoring, and ongoing improvement. Understanding syscalls is vital for optimising performance, enhancing security, and addressing complex issues, making them an essential focus for anyone exploring Linux internals.