Protection rings are a foundational concept in operating system (OS) design, essential for enforcing security, stability, and efficient resource management. They are hierarchical privilege levels used in modern processors to separate and protect various components of a system, such as the kernel, device drivers, and user applications.
In this article, we’ll explore protection rings in detail, including their origins, implementation in operating systems like Windows and Linux, the security they provide, and the challenges they face in the context of modern computing.
What Are Protection Rings?
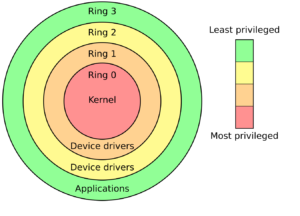
Protection rings are a system of hierarchical privilege levels built into CPU architecture, designed to separate different parts of a system to enhance both security and stability. Each ring dictates how much access code running within it has to system resources, ensuring that critical operations are safeguarded while minimising the impact of errors or malicious activities.
The rings are arranged from the most privileged to the least:
- Ring 0: Also known as kernel mode or supervisor mode, this is where the operating system kernel resides. It has full access to hardware and all critical system resources.
- Rings 1 and 2: These are often unused in modern operating systems but can be reserved for special purposes, such as device drivers or hypervisors in certain configurations.
- Ring 3: Known as user mode, this is where user applications and processes run with restricted privileges.
This layered approach ensures that code with higher privileges (closer to Ring 0) can directly manage hardware and critical resources, while lower-privilege code (Ring 3) operates in a restricted environment. By enforcing this separation, protection rings reduce the risk of accidental or malicious interference with core system operations, creating a more secure and resilient computing environment.
Why Are Protection Rings Necessary?
Protection rings play a crucial role in maintaining security, stability, and efficiency in modern multi-user, multitasking systems by addressing the following key challenges:
1. Process Isolation
- Protection rings prevent user applications from directly accessing hardware or critical system resources, ensuring system stability and reducing the risk of unintended interference.
2. Enhanced Security
- By enforcing strict privilege levels, protection rings mitigate the threat of malicious software compromising the kernel or other applications. This separation minimises the potential impact of vulnerabilities.
3. Efficient Resource Management
- Controlled access to memory, CPU, and I/O operations optimises system performance and prevents resource conflicts, allowing processes to run smoothly without interference.
4. Fault Tolerance
- Failures in user applications are contained within lower-privilege levels, preventing them from crashing the kernel or other critical system components.
Without protection rings, systems would lack these essential safeguards, making them highly susceptible to crashes, privilege escalation attacks, and security breaches. Their implementation is fundamental to the reliable and secure operation of modern computing environments.
History of Protection Rings
Protection rings originated as a solution to enhance security and stability in multi-user systems. Early computing lacked privilege separation, allowing applications unrestricted access to hardware and critical resources, which led to frequent crashes and vulnerabilities.
The Origins: Multics
The concept was formalised in the 1960s with the Multics (Multiplexed Information and Computing Service) operating system. Multics introduced eight privilege levels (Rings 0–7) to isolate the kernel, system functions, and user processes, laying the groundwork for modern operating systems despite its limited adoption.
Adoption in Modern Architectures
Modern architectures, like Intel’s x86, simplified this model to four rings (Ring 0 to Ring 3). Most systems, including Linux and Windows, use only Rings 0 (kernel) and 3 (user) for practical reasons, leaving Rings 1 and 2 largely unused. ARM architectures adopt similar concepts with different terminologies like privilege and exception levels.
Evolution with Virtualization
Virtualization added new privilege levels:
- Ring -1: Hypervisors like VMware and Hyper-V manage virtual machines here.
- Ring -2: Handles firmware-level tasks, such as system management mode (SMM).
Current Relevance
Protection rings remain integral to system design, isolating privileges to secure operations. Modern techniques like sandboxing, virtualization, and kernel hardening build on this model, ensuring resilience against evolving security challenges. This progression highlights how foundational concepts in computer science are continuously refined to meet modern needs.
How Protection Rings Work
Protection rings rely on CPU hardware to enforce privilege levels, ensuring secure and controlled access to system resources. Here are the key mechanisms that make this possible:
1. Current Privilege Level (CPL):
- The CPU tracks the privilege level of the code currently executing using the CPL field in its control registers.
- Lower-privilege code (e.g., Ring 3) cannot execute instructions or access resources reserved for higher-privilege levels (e.g., Ring 0), preventing unauthorised actions.
2. System Calls:
- Applications running in Ring 3 must use system calls to request services from the kernel in Ring 0.
- This controlled interaction ensures the kernel retains authority over critical operations while providing necessary services to user applications.
3. Interrupt Handling:
- Hardware interrupts, such as device signals, temporarily elevate the CPU to Ring 0 so the kernel can securely handle the event.
- Once the task is completed, control returns to the original privilege level, maintaining system stability.
4. Memory Protection:
- The CPU employs mechanisms like paging and segmentation to enforce strict boundaries between user-space and kernel-space memory.
- This isolation prevents user applications from accessing or modifying kernel memory, ensuring both security and stability.
These mechanisms work together to create a secure and efficient environment, isolating processes and safeguarding the system against accidental or malicious interference.
Security Benefits of Protection Rings
Protection rings play a vital role in safeguarding modern computing systems by enforcing strict privilege levels and isolation. Key security advantages include:
1. Privilege Separation:
Protection rings isolate user processes from the kernel, ensuring that applications cannot directly access or modify critical system resources. This separation acts as a robust barrier against unauthorized actions.
2. Attack Mitigation:
Privilege restrictions significantly reduce the risk of kernel compromise by limiting the impact of exploits targeting user applications. Malicious software in user space (Ring 3) cannot directly interfere with kernel operations (Ring 0).
3. Memory Isolation:
Protection rings enforce strict boundaries between user-space and kernel-space memory, preventing unauthorized access or manipulation of sensitive kernel data by user applications.
4. Process Containment:
Errors or crashes within user applications are confined to Ring 3, ensuring they do not affect the kernel or other system-critical processes. This containment preserves overall system integrity and stability.
Challenges and Limitations
While protection rings provide robust security, they come with certain challenges and limitations:
1. System Call Overhead
Switching between user mode (Ring 3) and kernel mode (Ring 0) introduces processing overhead. This can impact performance, especially in systems handling frequent system calls.
2. Kernel Vulnerabilities
If an attacker exploits a vulnerability to gain access to Ring 0, they can compromise the entire system. This makes securing the kernel a critical priority.
3. Underutilised Rings
Rings 1 and 2 are largely unused in modern OS implementations, leaving some CPU features untapped. While this simplifies system design, it also represents missed opportunities for finer privilege control.
4. Evolving Threats
Advanced attack methods like Return-Oriented Programming (ROP) and hardware-based vulnerabilities such as Spectre and Meltdown can bypass traditional protection mechanisms. These modern threats highlight the need for complementary security measures beyond protection rings.
While not a panacea, protection rings remain a foundational security feature, complemented by additional tools and techniques to address modern challenges.
Enhancements and Alternatives to Protection Rings
While protection rings provide a foundational layer of security, modern systems have evolved to address their limitations and counter emerging threats. Here are some key enhancements and alternatives that work alongside or independently of protection rings:
1. User Access Control (UAC)
- UAC restricts actions requiring administrative privileges, ensuring that critical changes to the system are intentional and authorised.
- By enforcing privilege elevation (e.g., requiring a password for administrative tasks), UAC reduces the risk of accidental or malicious system modifications in user space.
2. Kernel Hardening
- Tools like SELinux (Security-Enhanced Linux) and AppArmor implement Mandatory Access Control (MAC) policies, adding layers of security to kernel operations.
- These tools limit the scope of what processes can access, restricting the potential damage caused by compromised applications.
- Address Space Layout Randomization (ASLR) and stack canaries protect against memory-related attacks.
- Kernel patching techniques, such as Ksplice, allow for real-time updates to fix vulnerabilities without system downtime.
3. Virtualization
- Virtualization introduces new privilege levels, such as Ring -1, used by hypervisors like VMware, Hyper-V, and KVM. Hypervisors oversee guest operating systems running in their own virtualized Ring 0, isolating them from one another.
- This isolation ensures that a breach in one virtual machine (VM) does not compromise others or the host system.
- Technologies like Intel VT-x and AMD-V enhance virtualization security by creating distinct hardware-based privilege levels.
4. Sandboxing and Containers
- Sandboxing isolates applications in restricted environments, preventing them from accessing broader system resources. Tools like Firejail and Flatpak are widely used for sandboxing in Linux environments.
- Containers, powered by technologies like Docker and Kubernetes, provide lightweight virtualization by isolating processes, filesystems, and resources within a shared kernel. This minimises the risk of malicious code affecting the host or other containers.
- Security enhancements such as seccomp (secure computing mode) further restrict system calls available to containerised applications, reducing attack surfaces.
5. Hardware-Based Security Features
- Modern CPUs include features like Intel’s Trusted Execution Technology (TXT) and AMD’s Secure Encrypted Virtualization (SEV), which enhance isolation and protect sensitive operations.
- These features complement protection rings by safeguarding specific workloads, such as cryptographic operations and secure boot processes.
6. Microkernels and Separation Kernels
- Instead of running all kernel operations in Ring 0, microkernels minimise the codebase running in privileged mode, reducing the attack surface.
- Separation kernels take this further by isolating system components into separate domains, ensuring robust fault and security isolation.
7. Advanced Monitoring and Response
- Intrusion detection and prevention systems (IDPS) monitor kernel and user-space interactions in real time, flagging unusual behaviour.
- Techniques like anomaly detection and behavioural analysis strengthen defence against sophisticated attacks.
Final Thoughts
Protection rings are a cornerstone of secure system design, providing robust privilege separation and safeguarding critical resources. While challenges like kernel exploits and evolving threats persist, the combination of protection rings with modern security techniques ensures resilient and stable operating systems. Understanding protection rings not only deepens knowledge of OS internals but also highlights the importance of layered security in today’s complex computing environments.

