In today’s complex IT environments, managing and monitoring system events across a wide range of devices and platforms is crucial. This is where Syslog (System Logging Protocol) steps in as a standardized, efficient, and scalable solution for logging and monitoring. This post delves deep into what syslog is, why it matters, its inner workings, and how it can be effectively utilized.
What is Syslog?
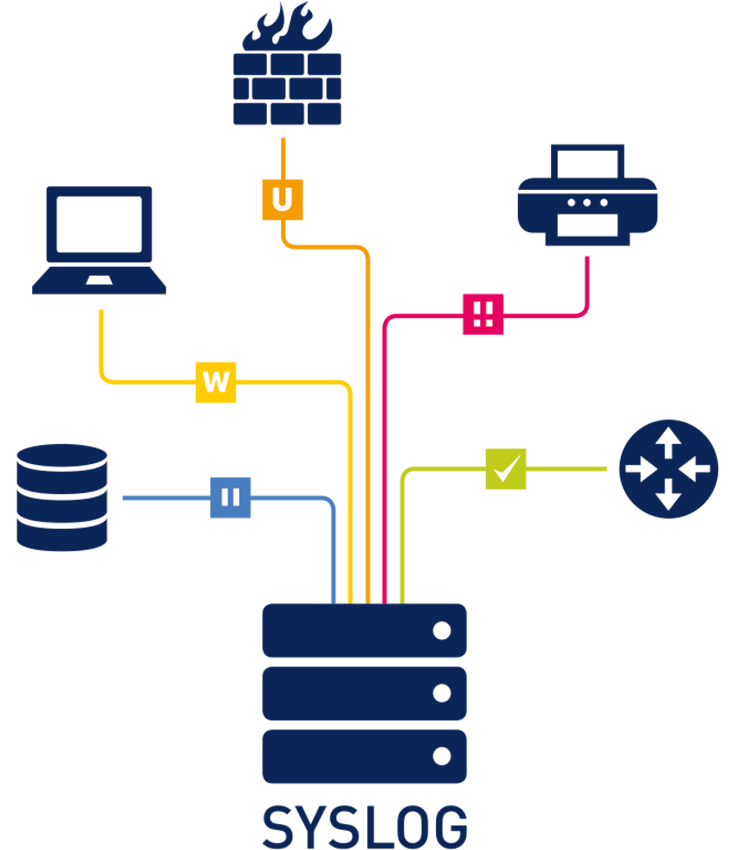
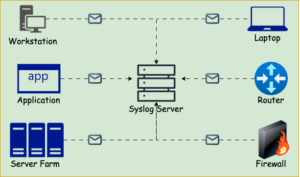
Syslog, short for System Logging Protocol, is a standard protocol designed to forward system logs or event messages to a centralized server, often referred to as a syslog server. By consolidating logs from multiple devices and systems in one location, syslog simplifies the process of monitoring and analyzing events, saving time and improving efficiency.
You’ll commonly find syslog integrated into network devices like routers, switches, firewalls, and even peripherals like printers and scanners. It’s widely used on Unix and Linux systems and by web servers like Apache. However, Windows systems rely on their native Windows Event Log and don’t support syslog out of the box. To bridge this gap, third-party tools or custom configurations can be used to forward Windows logs to a syslog server.
Why Syslog Matters
Managing logs across a sprawling network of devices can be daunting. Each device generates a multitude of events—errors, warnings, or informational messages—that need to be reviewed. Without a centralized logging solution, monitoring becomes chaotic, time-consuming, and prone to human error.
Syslog addresses this challenge by:
- Centralizing Logs: Aggregating logs from multiple devices in one location.
- Simplifying Monitoring: Enabling administrators to identify issues quickly.
- Supporting Automation: Integrating with tools for analysis and alerts.
- Enhancing Security: Detecting anomalies through consistent log review.
How Syslog Works
Syslog, defined by RFC 5424 as a replacement for the older RFC 3164, provides a robust and standardized framework for logging. Syslog operates on a client-server model:
- Clients: Devices (e.g., routers, servers, firewalls) generate and send syslog messages.
- Server: The syslog server receives, stores, and processes these messages for analysis.
Syslog messages are transmitted using either:
- UDP (default): Faster but lacks guaranteed delivery (port 514).
- TCP: Reliable delivery with confirmation (often port 1468).
Syslog messages are transmitted asynchronously, triggered by specific events rather than on a regular schedule, with conditions configured directly on the device, such as a router, switch, or server. Unlike protocols like SNMP, syslog does not allow for polling of data, although SNMP can sometimes be used to modify syslog parameters remotely.
Syslog Message Format
Syslog messages follow a structured format, ensuring consistency across systems.
Message Components:
- Priority (PRI): Indicates the facility (source) and severity level.
- Header: Includes the timestamp and hostname/IP of the device.
- Message (MSG): The main log body, containing the application/process name (TAG) and event description.
Example:
<34>1 2022-11-07T12:45:30Z webserver.example.com nginx - - - Connection from 192.168.1.1 accepted
<34>: Priority (Facility: Syslog, Severity: Informational).1: Syslog protocol version (RFC 5424).2022-11-07T12:45:30Z: Timestamp.webserver.example.com: Hostname of the source device.nginx: Application generating the log.Connection from 192.168.1.1 accepted: Event description.
Security Considerations
The syslog protocol lacks any inherent security mechanisms, leaving it exposed to several vulnerabilities. It does not include authentication to verify the origin of messages, making it possible for malicious actors to impersonate devices and inject false log entries. Additionally, syslog transmits data in plaintext, offering no encryption to protect the information being sent to the server, which makes it susceptible to interception and unauthorized access.
A notable risk is its vulnerability to “playback attacks,” where an attacker replays a previously captured stream of warnings or events to provoke unnecessary responses or mislead administrators. Without added layers of security, such as encryption (e.g., TLS) and access controls, syslog’s lack of built-in protections can pose significant challenges in environments where the integrity and confidentiality of log data are critical.
Configuring Syslog for Effective Use
Device Configuration
Syslog is highly configurable, allowing you to decide which facilities (sources of messages, such as applications or system components) and severity levels (e.g., errors, warnings) generate syslog events that are forwarded to the server. Proper configuration is crucial to prevent overwhelming the server and network with unnecessary traffic. For instance, setting the severity level to “Debug” should only be done during testing, as it generates an excessive number of messages.
To optimize syslog traffic, configure devices to forward only the most critical events. For example, a router might be set to report errors, such as a downed interface, as these are high-priority events that require immediate attention. In contrast, a network printer could be configured to log only critical issues to avoid unnecessary noise. Adjusting these parameters based on the importance of the device and the nature of the events ensures efficient monitoring.
Syslog on Windows
Unlike Unix and Linux systems, Windows does not natively support syslog within its Event Log system. However, you can still forward Windows events to a syslog server using third-party utilities. These tools monitor the Windows Event Log, translate the events into the syslog format, and forward them to the server using the standard syslog protocol. This approach enables Windows systems to integrate seamlessly into centralized logging setups.
Limitations of Syslog
While syslog is a powerful logging tool, it has notable limitations. One significant drawback is that the device being monitored must be operational and connected to the network to generate and send syslog events. For instance, a critical kernel error may not be logged at all if the system crashes and goes offline before the message can be transmitted. As a result, syslog is not suitable for monitoring the availability (up/down status) of devices. Alternative tools, such as SNMP or specialized monitoring solutions, are better suited for tracking device status and uptime.
Conclusion
Syslog is a cornerstone of modern logging and monitoring systems. Its ability to centralize logs, ensure consistent formatting, and integrate with analysis tools makes it invaluable for infrastructure and network management. By understanding its components, architecture, and security considerations, you can harness the full potential of syslog to enhance visibility and maintain control over your environment.
Stay tuned for more insights on implementing and optimizing syslog in your infrastructure! 🚀